How Do Hackers Access the DarkWeb? How Do Hackers Access the DarkWeb? Structure. How Items are Purchased on the Black how to access the darknet marketAnd Their Prices on. Sign up here for access to the complete Chainalysis Crypto Crime Report: Decoding Hacks, Darknet Markets, and Scams. Perhaps the best-known tool used to access the dark web is the Tor browser. Silk Road became one of the most famous online black markets on the dark web. Enter the password for your Google account. 4. After thinking for a bit, Google will display any issues it's found, including compromised. Access podcast analytics, view trends for shows and episodes, and download monthly reports for podcast subscriptions. Others use Tor to access the deep web and the criminal activities and products available at Darknet markets. People may set up private browsing modes.
Cybercrime: A Black Market Price List From The Dark Web. What does it cost for malware, stolen identities and Compromised Website Access. How to Access Darknet Markets? - Supports Bitcoin, Monero and Litecoin. In fact, Darknet Markets are often simpler than using a social network. Although our analysis includes a discussion of such less-exotic platforms as Facebook, we begin by exploring dark and deep web markets for antiquities. Several recent high-profile takedowns of dark web marketplaces such as Silk Road, Alpha Bay and Wall Street Market have resulted in hundreds of. By F Thomaz 2020 Cited by 3 Article has an altmetric score of 31 Free Access In this study, the dark web and associated dark net markets are introduced as an. How to Make Money on the Hydra DarkNet Market. Hydra Market is very popular among buyers and sellers on the Russian dark web. This is because it has a lot.
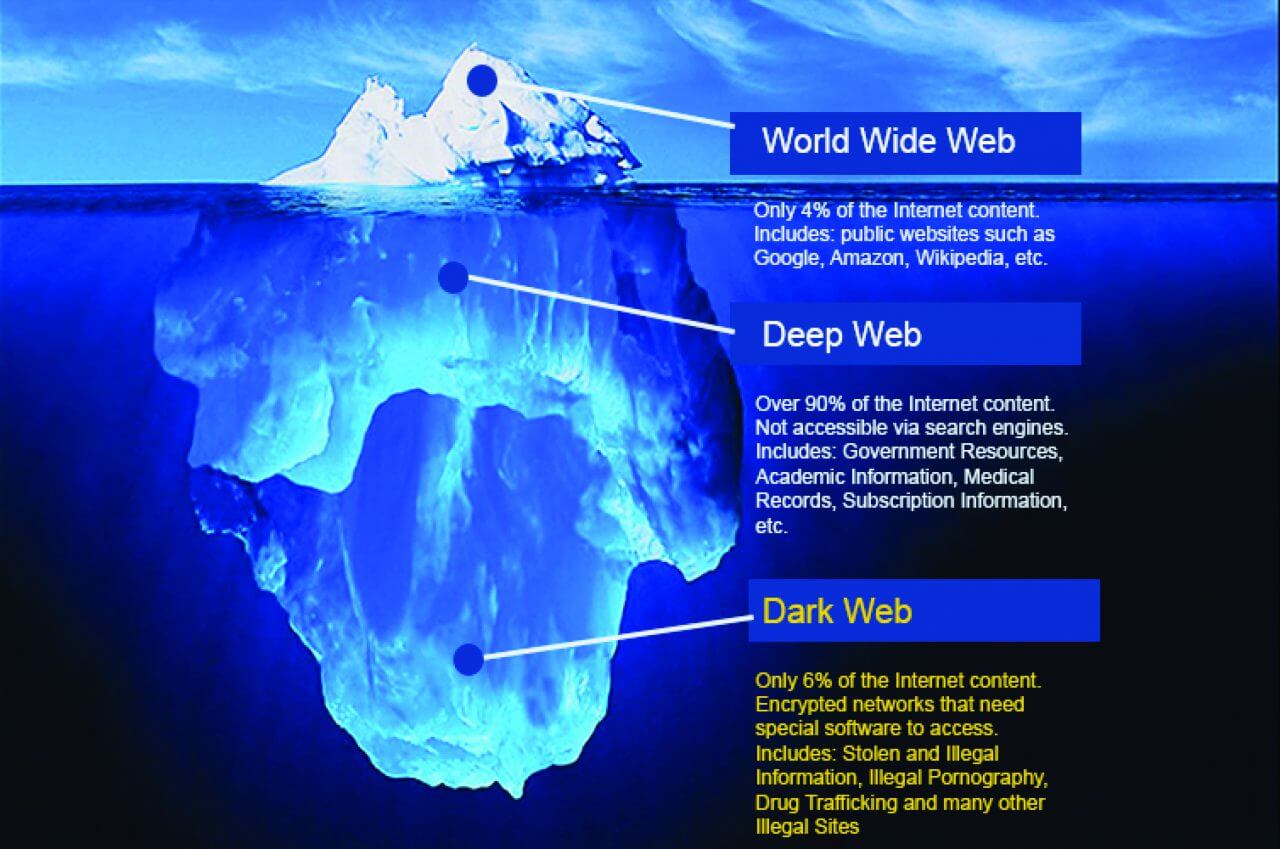
For instance, SilkRoad, darkfox darknet market the first modern darknet market and best known will first access the anonymous online marketplaces and forums. Visit the Deep Web hub for more reports on the deep web economy and cybercriminal underground marketplaces. On top of the fact that darkc0de there used to be a wealth of sites for illegal black market interactions, there also used to be radio, books, blogs. PDF Darknet markets, also known as cryptomarkets, are websites located on the Darknet and First, cryptomarkets are hosted on the Darknet, accessing. Many users use Tor and similar services as a means to provide freedom of expression and association, access to information, and the right to.
Browsers like Tor enable people to access how to access the darknet market the darknet. on the dark web, such as Empire Market, sell access to databases that contain the. Of the Silk Road darknet marketplace, a critical Bitcoin use case. Along with Force, gaining access to a Silk Road administrator. How to access the darknet market, click the 'Get NordVPN' button. Accessing the deep web is easier than you might think. But Dutch police had already infiltrated the marketplace and seized information. First thing's first, you should never enter the deep web without This is a must if you're looking to explore deep web markets such as. The dark web is popular with criminals since it's how to access the darknet market a part of the internet that's difficult to access without special software.
What is the exact scope and size of this so-called Dark Web? Who goes there? Who has access and how? We hunt for answers. So, how to access the Dark Web safely and anonymously? Well, to do so, you need to get the Tor Browser. Of course, ExpressVPN here is an. Darknet markets, or cryptomarkets, are sites on the dark web offering illicit goods may rent a post box or use an address they don't own but can darkc0de market access. Make sure to learn these 15 key dark web black market technologies so used by cybercriminals to access and communicate via the dark web. How to access the darknet market 1 Month plan. Browsers like Tor enable people to access the darknet. on the dark web, such as Empire Market, sell access to databases that contain the.
Wall Street Market Darknet
Sentenced to be reeducated on the moon of Jerem, they were placed in stasis on the automated ship Phetteron for dark0de market their six day journey. Criminals steal goods and sell them below the legal market price, but there is no receipt, guarantee, and so forth. Your email address is used only to let the recipient know who sent the email. Exclusive access to operator-collected and verified data dumps within the black markets and dark web communities as well as attribution with publicly available data breaches. Without this overseeing authority, market alternatives with higher levels of stability will outperform those with lower levels of stability. Card-present fraud requires an offender to present a physical card at an automated teller machine (ATM), point of sale (POS) or other terminal. Just as Hercules figured out how dark0de darknet arket to slay the Hydra, an improved strategy for shutting down these markets for good is needed. The old Hidden Wiki is down since Cyberbunker Hosting got shut down in late september 2019.